Resources
Integris Engage
Find resources, links to events, and more on our one-stop education platform.
Register for upcoming events
Explore in-person and virtual upcoming events hosted by Integris
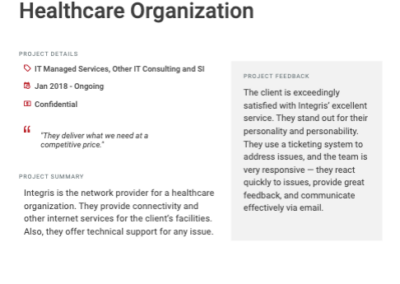
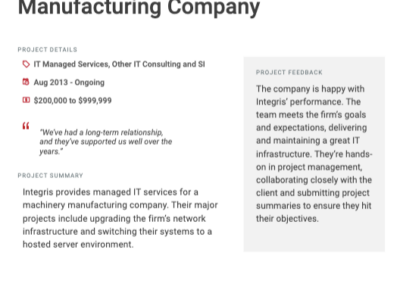
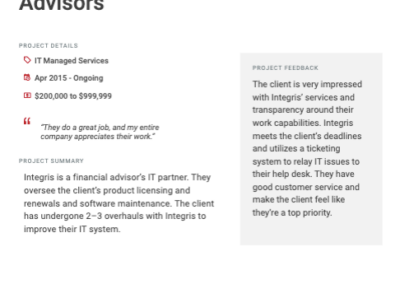
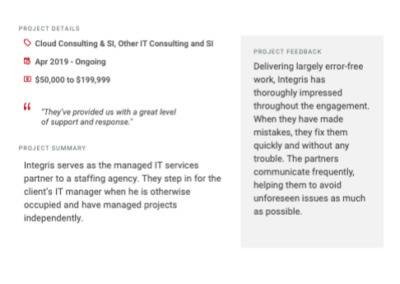
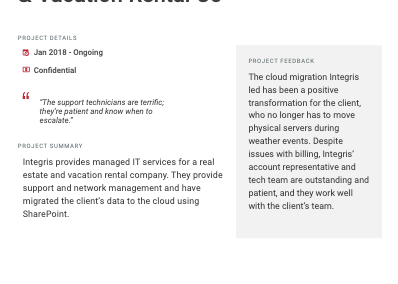
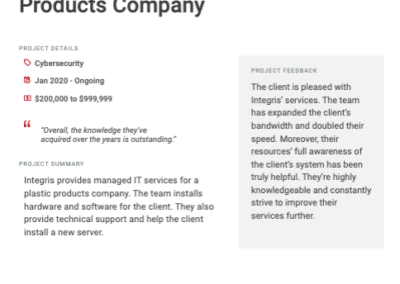
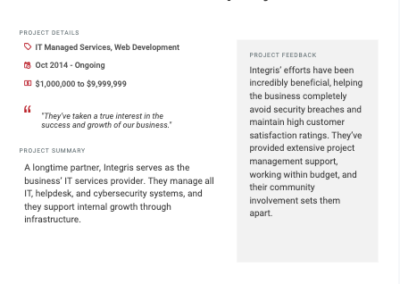
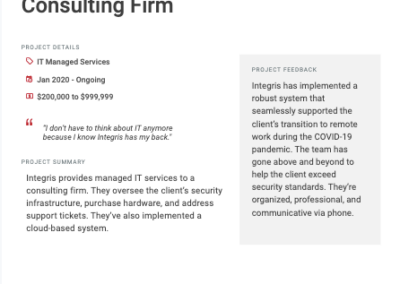
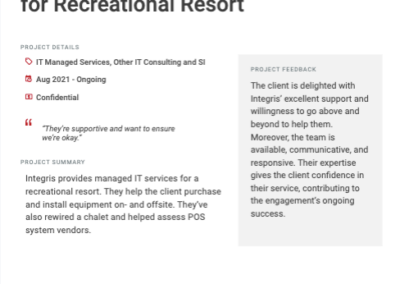
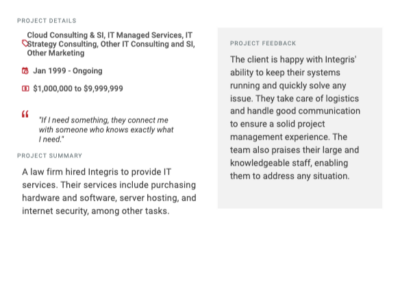
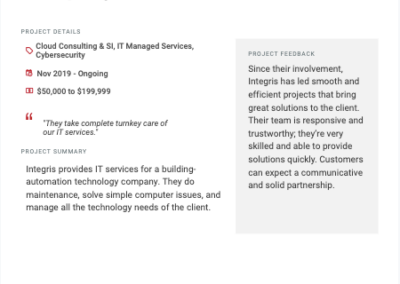
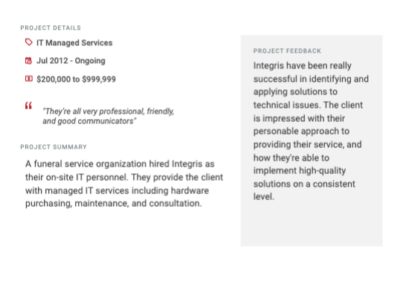
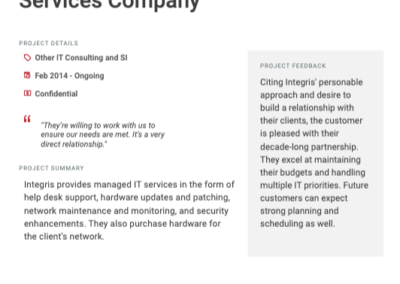
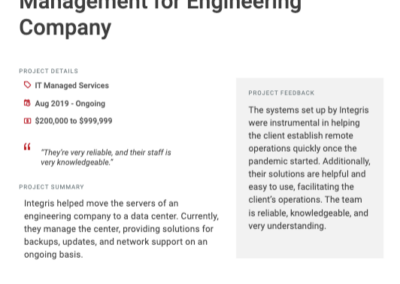
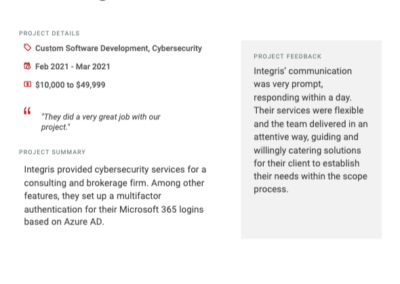
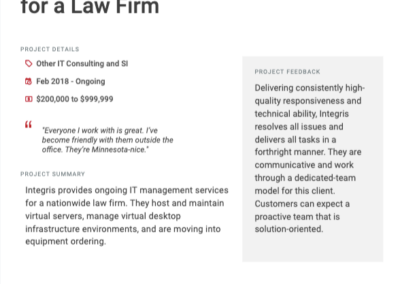
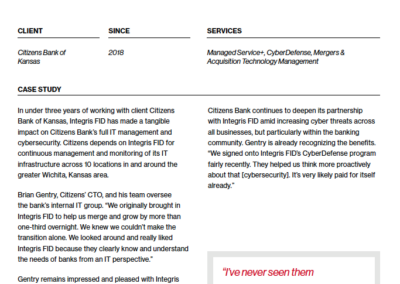
Client testimonials
Independent reviews
Keep in touch
Join our newsletter
Follow us on LinkedIn
Subscribe on YouTube
Blogs & reports

REPORT
Understanding U.S. Banks’ Annual IT Spend in 2024
Identifying benchmarks and top strategic priorities from thousands of bank executives
Blog
Blog
All blogs
Explore the entire Integris blog archive
Buffalo-Plaid Breakfast
Coffee & cybersecurity talk. Tune in every Friday, 9 AM ET for the latest episode.
Upcoming digital events
Creative Kickstart: Artificial Intelligence
Friday, May 3
1 PM EST / 12 PM CST / 11 AM MST / 10 AM PST
Use AI to improve your written words, write articles, create presentations, generate event descriptions, produce blog content, make social media post copy, create images, design email campaigns, analyze your data for reports, and even make audio and video clips.
Upcoming in-person events
Integris Inspire
Multiple dates throughout 2024
Next: April 25 / Atlanta, GA & June 11 / Duluth, MN
10+ events across the country
Join Integris for a day that will take your business to the next level – network with business leaders and IT experts, learn with panels and small group sessions that bring the best strategic technology advice that your organization needs to thrive.

Austin FC
Wednesday, May 29

Topgolf Fort Worth
Thursday, June 13

Rochester Red Wings
Thursday, June 13

Topgolf Denver
Tuesday, June 25
PINSTACK San Antonio
Thursday, June 27
Topgolf Baltimore
Tuesday, July 11